We have collected a whole new crop of virus-themed emails, several of which were alarmingly extreme in the claims they made while pitching their products, services, and, of course, malicious social engineering campaigns.
The United States Secret Service just put out a press release to warn against a wave of Coronavirus scams: https://www.
Given how rapidly bad actors are ramping up their efforts to exploit the coronavirus health crisis, we thought it would be useful to give readers yet another peek at what we’re seeing.
More Spammers, More Scammers
One email we hadn’t yet seen when we published our initial review of virus-themed emails was the one we had been sure would eventually arrive. On Tuesday it did: the dodgy email requests for charitable donations.
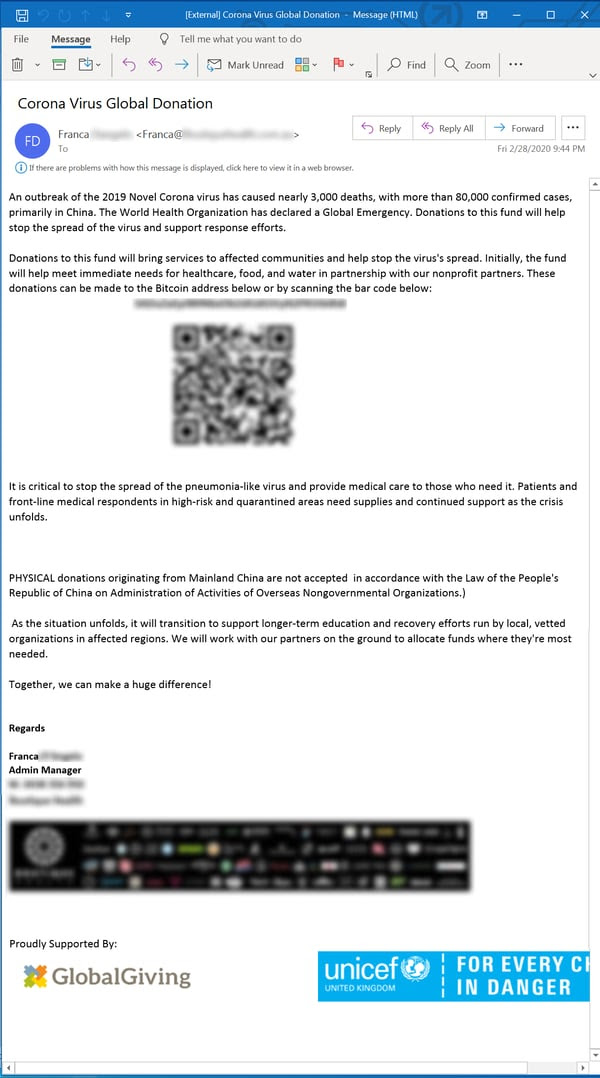
This one even comes complete with a QR code to speed the process of emptying your wallet for an outfit that claims to have the backing of well-known organizations like GlobalGiving and UNICEF.
The pitch used in the above email is fairly routine as charity-focused emails go. By contrast there is nothing routine about some of the other spam/scam emails reported to us.
Take, for example, this rather bracing email, which dangles the prospect of secret knowledge about the unfolding crisis — a manipulative tactic usually seen in aggressively paranoid scam emails for things like quack medical treatments, get-rich-quick schemes, perpetual energy machines, and dark revelations about the machinations of the Deep State.
More Bad Guys, More Phishes
Mad and malicious missives from bad actors aren’t the only coronavirus-themed emails we’ve been seeing. In fact, there has been a veritable explosion of emails from legitimate organizations messaging customers, clients, and employees about the situation — offering statements, newsletters, news portals, dedicated web pages, and even webinars. Indeed, among the most sought-after items among citizens and users — setting aside medical products, of course — is plain old information.
Information was the motivational motor that drove the social engineering schemes deployed in the very first outright malicious emails we started seeing back in early February. As legitimate organizations continue filling users’ inboxes with news updates, tips, and advice, the offer of new information remains perhaps the easiest, most obvious and effective angle that malicious actors continue to work.
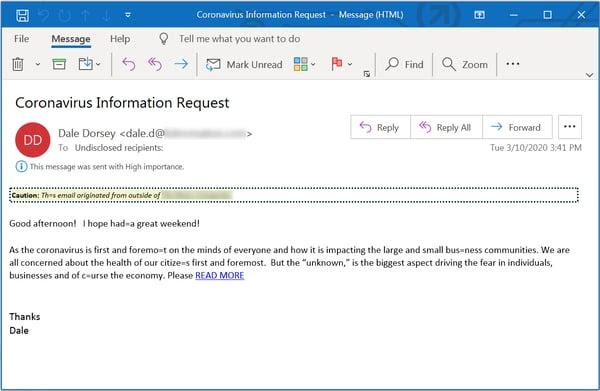
What’s striking about this email is that it’s not even clear who Dale is and what his alleged relationship with readers might be. No matter, Dale will be addressing the “unknown” aspects of the crisis, so why don’t you just click that link to READ MORE.
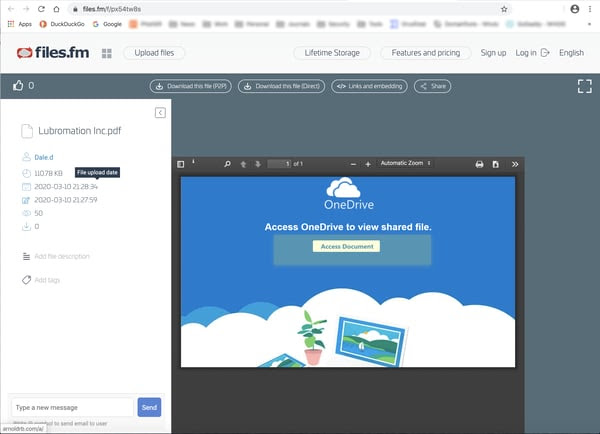
The first hop on the road to COVID-19 enlightenment is a file-sharing site with a slickly designed document that inexplicably asks users to click through to yet another file-sharing host — Microsoft’s OneDrive (now apparently hosted on a .XYZ domain). OneDrive, of course, requires a login.
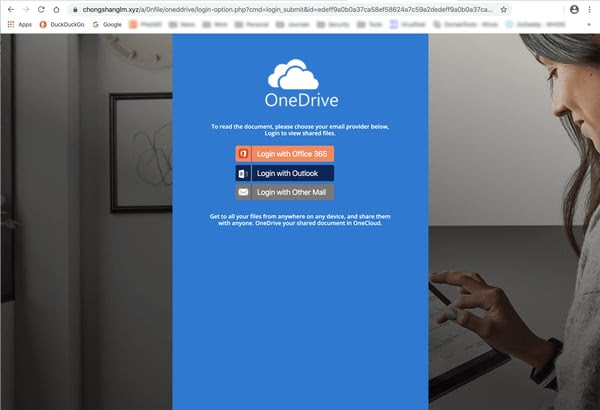
Yep, it’s the old credentials phish, always ready and willing to harvest whatever credentials you happen to bring to the table. To be sure, there are plenty of red flags in this phish, from the initial email all the way through to the final landing page. How many anxious, fearful users will even notice, though?
As we’ve noted in other blog posts, the bad guys are very keen observers of Western business culture, and they’ve figured out that organizations are increasingly turning to informal surveys — usually run through services like Energage, SurveyMonkey, Qualtrics, and even the form-building offerings from Microsoft and Google — to help manage their relationships with employees.
On Monday of this week we started seeing organizations hitting their employees and users with a special round of coronavirus surveys to register their concerns, questions, and general level of anxiety. As per usual, these surveys tended to hail from HR departments and IT departments — both favorite targets for spoofing by malicious actors.
To no one’s surprise and less than twenty-four hours later we spotted our very first fake coronavirus survey from the bad guys…
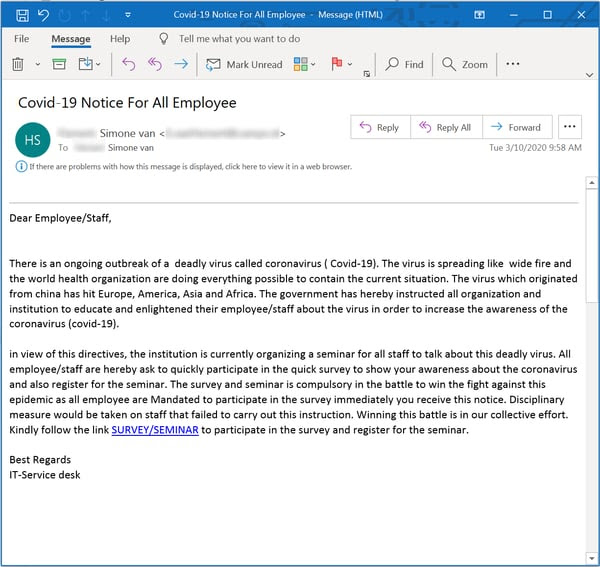
Although the IT-Service desk is still a little shaky with capitalization and spelling, they do have a Survey/Seminar for you. And even though you’re already logged in to your workstation and email, you will have to log in yet again through the organization’s OWA instance.
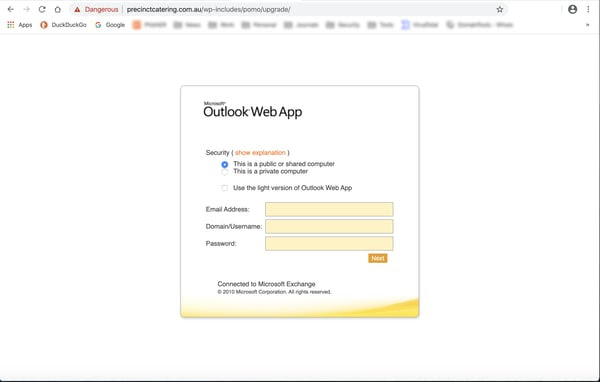
As before, we have to wonder how many users will even blink before clicking through and coughing up their login credentials.
Conclusion
For bad actors across the internet, the coronavirus is the gift that keeps on giving — providing endless opportunities to separate anxious and concerned employees from their logins and their money, all while persuading them to open the door to your organization’s mission critical network.
If your organization has already been messaging its employees with news, updates, tips, and advice, it behooves you to also warn and educate them about the dangers posed by bad actors trailing in the wake of the virus and looking to exploit fear, paranoia, and ignorance through social media posts, dodgy web ads, and fraudulent emails.
Your organization is likely already dealing with the several new challenges posed by the coronavirus and its spread across the globe. There’s no reason to let those challenges be compounded by a threat that is not so novel or new — malicious actors looking to cash in through whatever means necessary.

